On April 14, 2025, the KiloEX protocol suffered a loss of $ 7.5 million for significant violations of security. This event comes from the Oracle operation attack and emphasizes the important vulnerabilities of the protocol access control mechanism. Let’s find out what happened and what we can learn.
Root cause
The root of the exploit was the access control of the protocol. MinimalForwardercontract. Contract inherited from Openzeppelin ‘s MinimalForwarderUpgradeable It contains vulnerabilities executeA function that does not correctly check the signature of the data provided.
Trust model
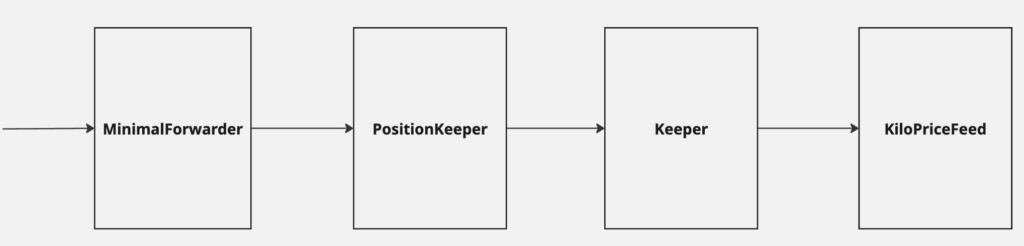
The KiloEX protocol was operated as a complex trust model related to multiple contracts.
- KilopriceFeed → Goalkeeper
- Goalkeeper → Position Keeper
- Position Keeper → Minimum forward
- Minimum forward → Unlimited access
Critical defects are in the final link of this chain. MinimalForwarder contract I trusted the request that comes in.
Attack vector
The attacker exploited vulnerabilities by producing malicious transactions that detour intended access controls. You just need to offer the attack successfully.
- valid
fromAddress (it can be obtained from previous transactions) - valid
signature(Also observed in the warm chain data) - All arbitrary
toAddress (in this case Position keeper)) - custom
dataTo run the function
Especially this attack MinimalForwarder The contract was not transparent and could not be found on the BSC or base.
Running attack
The attacker has been exploited through a series of calculated stages.
- We manipulated Oracle to lower asset prices.
- I opened a long position at an artificially low price.
- In order to raise the price, we manipulated Oracle again.
- Closed location for significant profits
Influence and meaning
This case reminds me of some important security principles.
- Access control is important Even inherited contracts require careful review and potential modifications to meet specific security requirements.
- Trust model verification -The complex trust relationship between contracts requires thorough verification at each stage.
- Oracle security -The price feed mechanism remains an important attack vector in the Defi protocol.
Evidence
The attack has been run in several chains.
Binance Smart Chain:
base:
Main takeout
- Always review and test inherited contracts, especially access control mechanisms.
- For security analysis, you should be able to identify and access contract implementation.
- It is dangerous to rely on a single access control point. Implement a deep defense.
conclusion
For protocols to prevent similar events:
- Implement a strong signature verification in the contract delivery
- Keep a clear document on trust relationship between contracts
- Regular security audit focused on access control mechanisms
- Consider the implementation of the circuit breaker for significant price fluctuations.
This event shows the potential result of overlooking the importance of thorough security and the development of smart contracts.

