Analysts of Global Ledger said about 46%of the hacked funds are idle and suggest a recovery after the accident.
The hacker is still fast, but the system is still followed. The new report of the blockchain Intelligence company, Global Ledger, is a new report based on hundreds of on -chain cases, and in many cases the stolen funds were stolen before the hacking was released before the land was stolen before the land was released.
According to a report shared with Crypto.news, it takes 43.83 hours from the initial chain violation on average until the victim project or the third -party investigator reports the case. Meanwhile, hackers tend to move the stolen funds to the first identification company, such as exchange, encryption mixers or distributed financial protocols.
But the longest delay is the window between public disclosure and the interaction of the attacker with the laundry service. This is an average of 78.55 hours, suggesting that funds are already well known before hacking is widely known.
‘There is no clear playbook here’
Overall, researchers at Global Ledger have measured four major timelines across hundreds of events. Time from violation, violations, reports, violations, first entity interactions, and public release to laundry activities. Each delay also talks on its own story.
For example, attacks on NFT projects show the slowest fund movement. On average, the funding of this abuse takes 563.63 hours or almost 24 days to move to the first known company of the laundry chain. This is more than twice the average delay in the centralized exchange -related hacking and records the clock in about 425 hours.
The co -founder and CEO Lex Fisun of Global Ledger says that in the NFT’s exclusive commentary on Crypto.news, the long delay says that these tokens are “uniquely and quietly off.”
“There is no clear playbook. Wash usually includes laundry or social engineering. The attacker has emitted $ 340,000 from Steth but remember the idol exploitation attached to the relevant NFT.”
LEX FISUN
This report emphasizes how the washing path changes depending on the exploited project type. The Defi platform and token generally see the money moving through the laundry channel within 230 hours, and the payment platform shows the fastest processing time, which is only 0.6 hours. Game and meta exploitation is one of the fast trends within 25 hours.
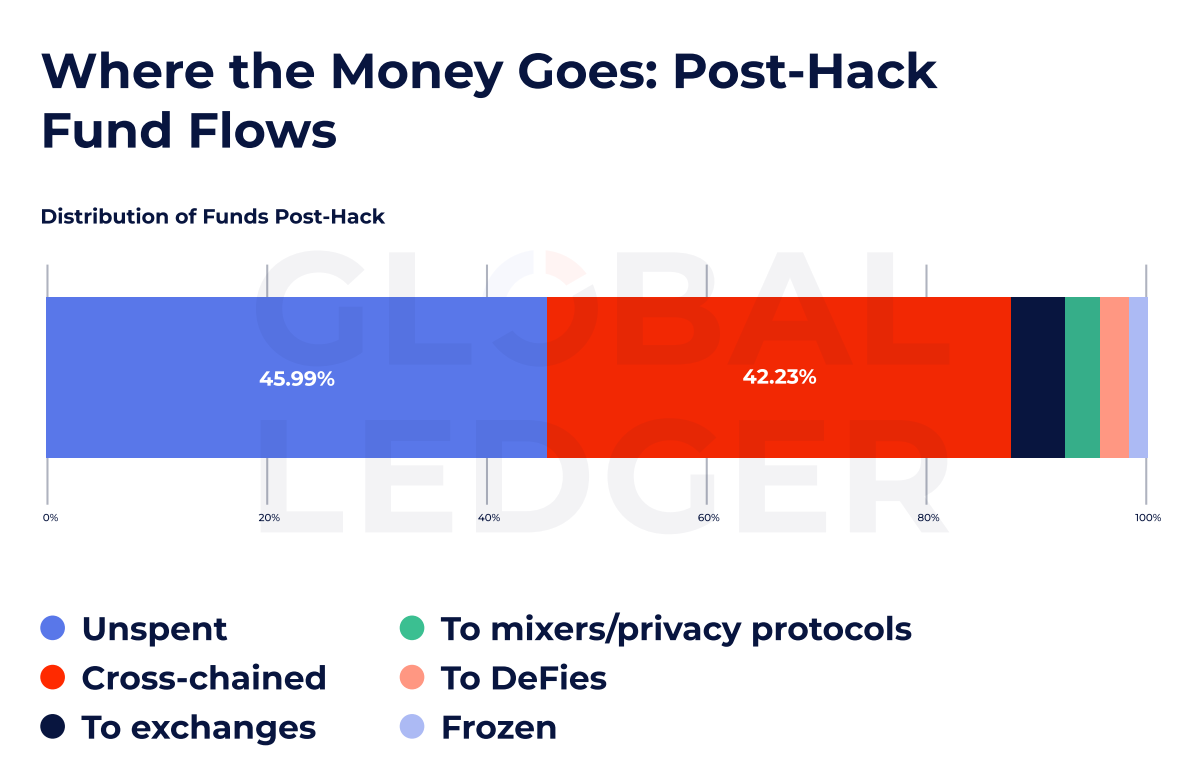
Despite the speed and fragmentation of the fund flow, the amazing amount of amazing hacking assets did not touch. According to the data, almost 46%of theft funds are still unstable, suggesting that there are significant opportunities for long -standing tracking and potential recovery after the incident occurred.
Cross chain trace
While many funds are idle, they are slipping through cross chain lines, where more and more market share is difficult to track. This report shows that 42.23%of thefts crossed the chain and bypassed the monitoring system for each chain.
FISUN explained that the cross chain Bridge has already slipped the chain -star monitoring and has already become one of the best funds laundry tools. And repeated abuse can lead to AML investigations, but the tornado cash case is “sanctions shift tactics, not demand.”
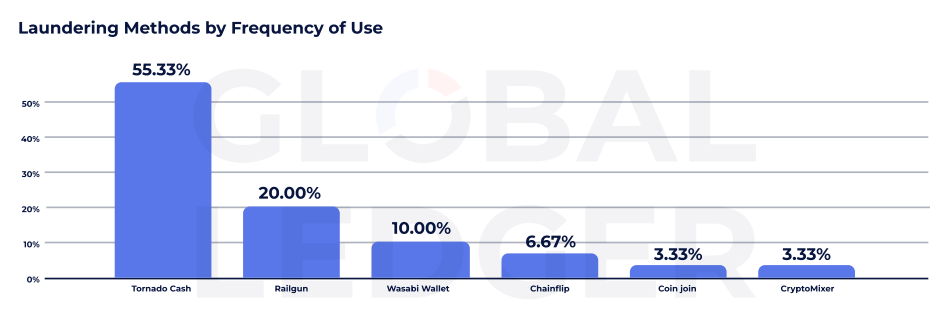
According to the data from Global Ledger, tornado cash remains a dominant laundry protocol used for more than 50% of the company’s traces. Despite the sanctions of the US Treasury in 2022 and the pressure of regulators around the world, the service continues to play a central role in post -laundry.
After the US court ruling, the use of the constitutional basis in 2024 reversed the use.
Other personal information protection tools are also gaining momentum. For example, Railgun was used in 20%and Wasabi wallets were 10%. According to the data, Chainflip, Coinjoin and Cryptomixer are involved in less than 7% of the laundry, respectively.
The attacker becomes smarter
FISUN does not only reflect better compliance with a slow flow through the centralized exchange (currently 425 hours or more).
The CEO of the Global Director added that the attacker divides assets and uses personal information protection protocols to move the stolen funds through the “attempt to delay the brilliant flow”, “the slow timeline is” not a defect but a design. “
Execution or compliance teams are only frozen. The report suggests that real -time response remains rarely despite the development of analysis and monitoring tools.
The number emphasizes a place where only the defender can take advantage of continuous challenge. Sometimes the time interval measured shows that there is still a space to act before the theft disappears completely.

