Solana development is progressing quickly. Contracts go from local testing to mainnet in a matter of days. But speed brings risks. Missing signer verification or overlooking an untested edge case can cost you millions of dollars.
Today we’re releasing the first VS Code extension built explicitly for Solana developers. It provides two essential layers of security directly into your editor. Real-time static analysis and fuzz coverage visualization. Get instant feedback as you code without additional tools or CI/CD delays.
what is it
The Solana VS Code extension adds security-focused development tools to your existing workflow. It performs two main functions:
Real-time security analysis Catch common Solana-related vulnerabilities as you type. Built on real-world production audit results, nine detectors flag issues such as missing signer verification, insecure math operations, and improper account initialization before even compilation.
Fuzzy range visualization It shows some code path. trident The test actually runs. Green highlights indicate obscured lines. Red highlights indicate untested paths. The execution count shows how thoroughly each line has been tested.
Both features are integrated directly into VS Code without any configuration. When you open a Solana project, the extension works immediately.
Real-time security analysis
Rust extensions can catch syntax errors. We are unable to detect any security issues related to Solana.
Consider the following code:
#(derive(Accounts))
pub struct UpdateConfig<'info>
#(account(mut))
pub authority: AccountInfo<'info>,
#(account(mut))
pub config: Account<'info, Config>,
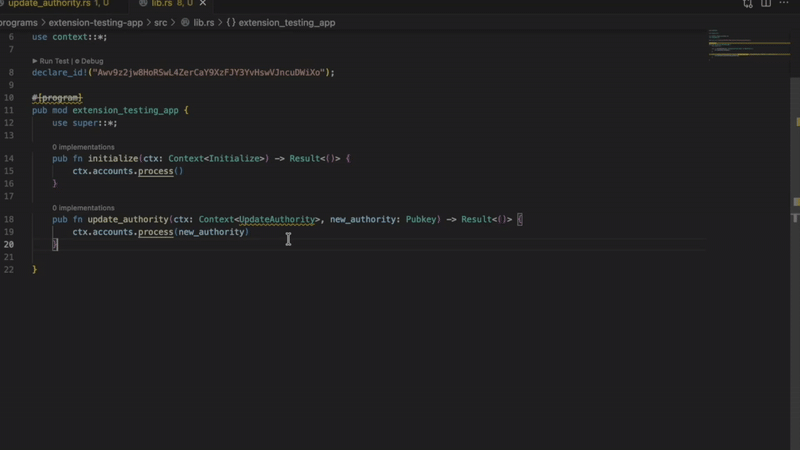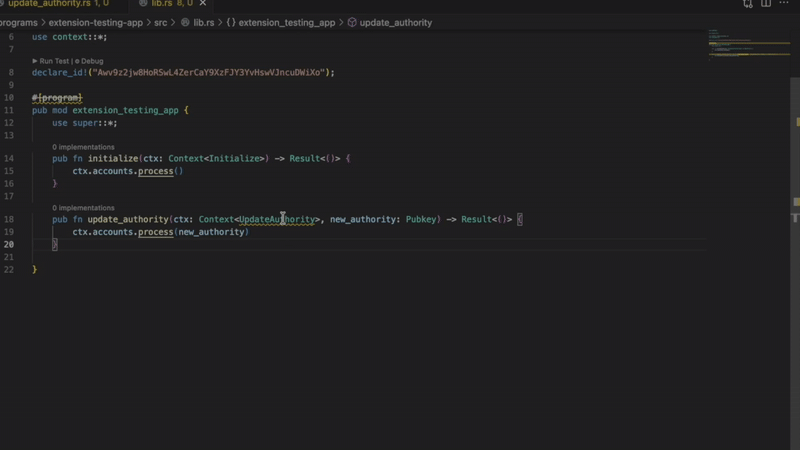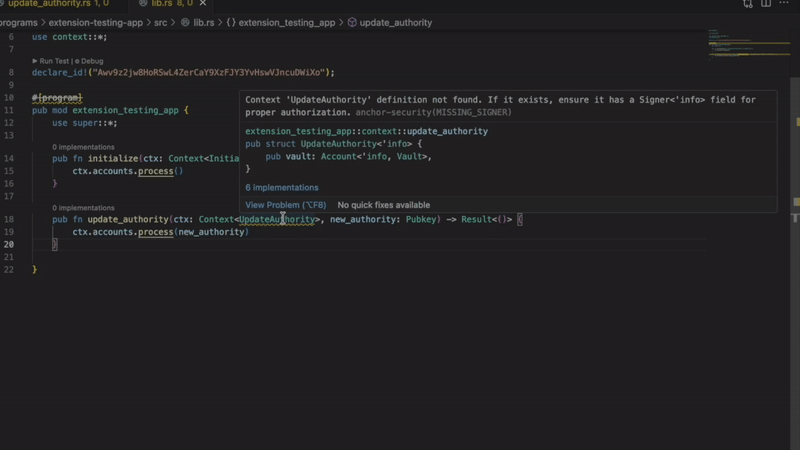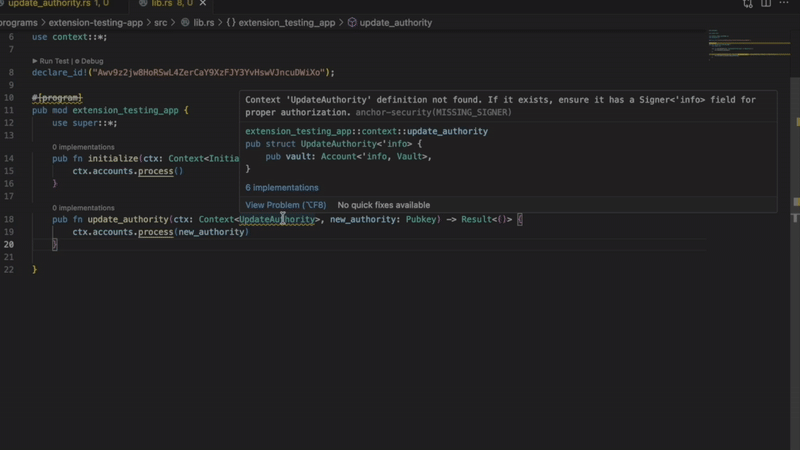
It compiles. It runs. However, there are significant vulnerabilities. The problem is that privileged accounts lack signer verification. Anyone can call this command and modify the configuration.
The Solana extension immediately flags you with a red wavy line and an accurate diagnosis. “Privilege account is missing signer verification.”
9 detectors
Each detector targets vulnerabilities discovered in actual Solana protocol audits.
- Missing signer verification
Catch accounts that require signer verification but do not have signature verification. Without verification, privileged functions become public.
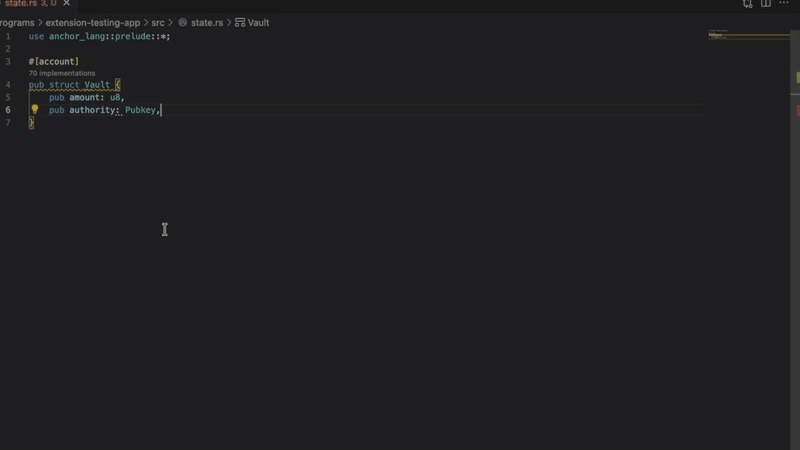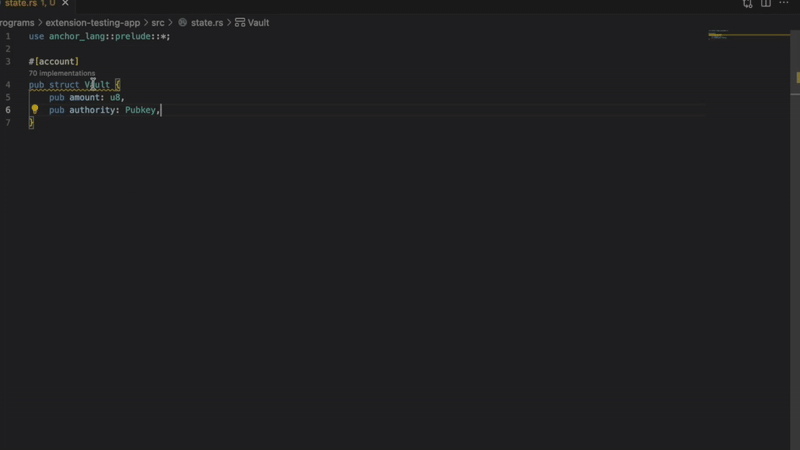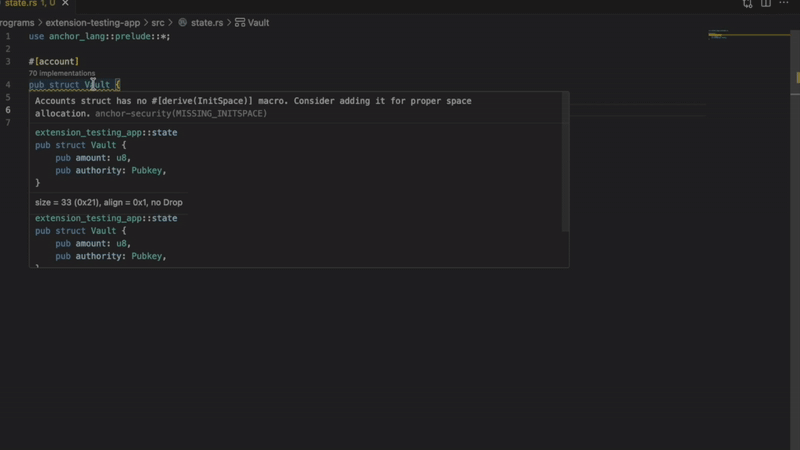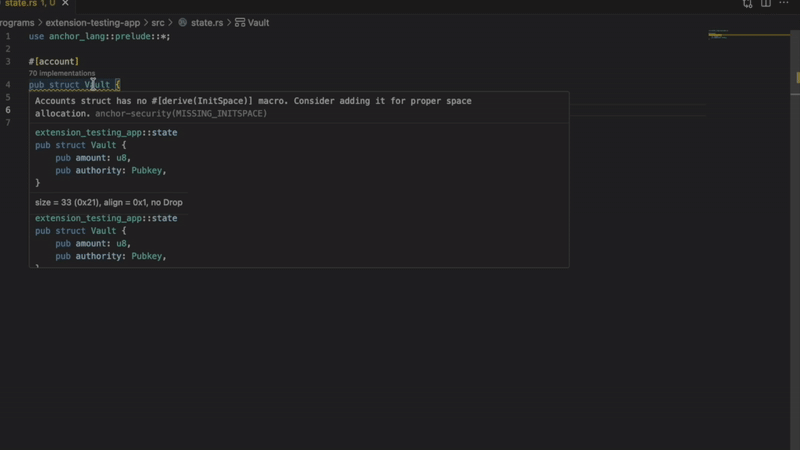
- Missing InitSpace
Detects account creation without proper space initialization. Prevent runtime errors when your account does not have enough space allocated. Important for programs that use Anchor’s reset forcing.
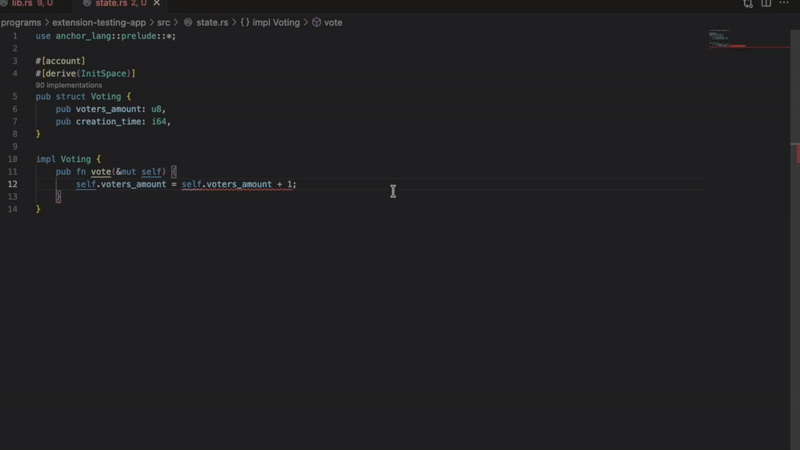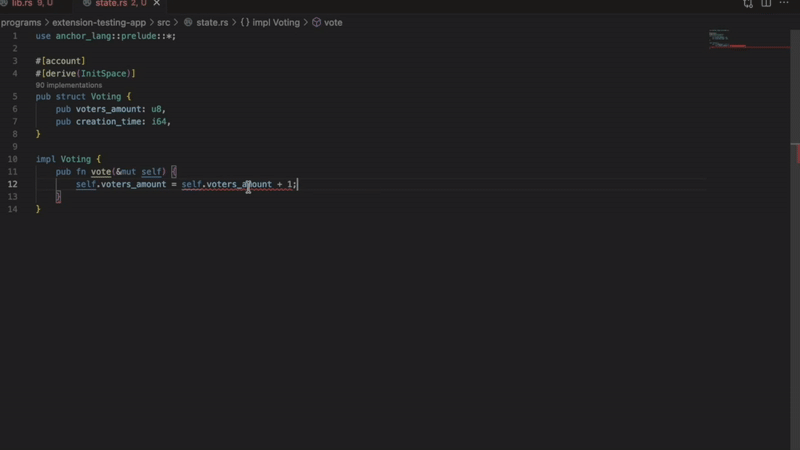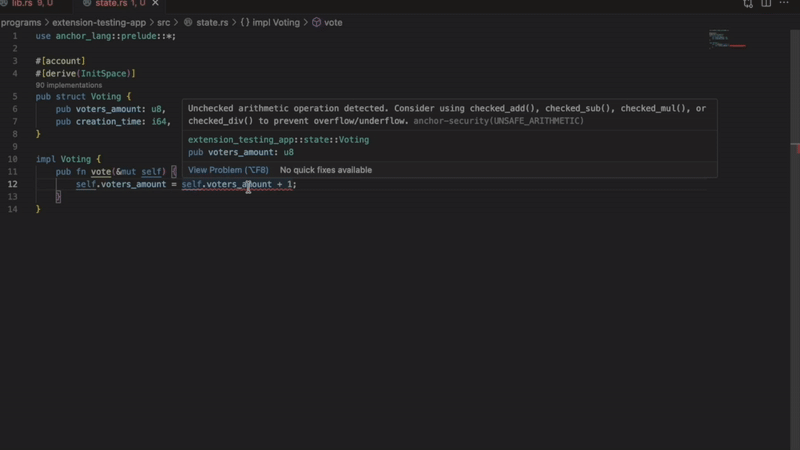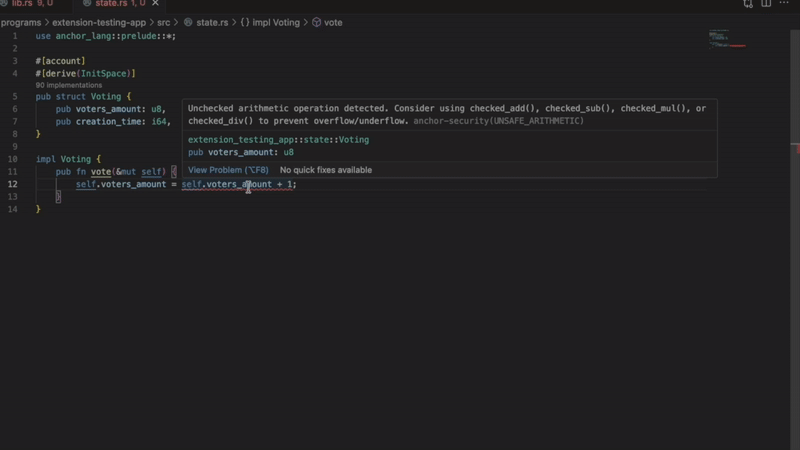
- unsafe math operations
Flags operations that may overflow or underflow.
let total = amount1 + amount2; // Flagged - no overflow protectionThe extension suggests using: checked_add(), checked_sub() or checked_mul() Instead.
- Manual lamp zeroing
Detects unsafe manual lamp operation. Manually zeroing the lamp may bypass security checks and introduce vulnerabilities. The extension recommends using an appropriate closing pattern.
- Account variants that cannot be changed
Captures attempts to modify accounts marked as immutable.
#(account)
pub config: Account<'info, Config>, // Immutable by default
// Later in code...
config.update(); // Flagged - attempting to mutate immutable account- Invalid command attribute
Detect misconfigured command properties. Prevents runtime errors due to incorrect instruction definitions before compilation.
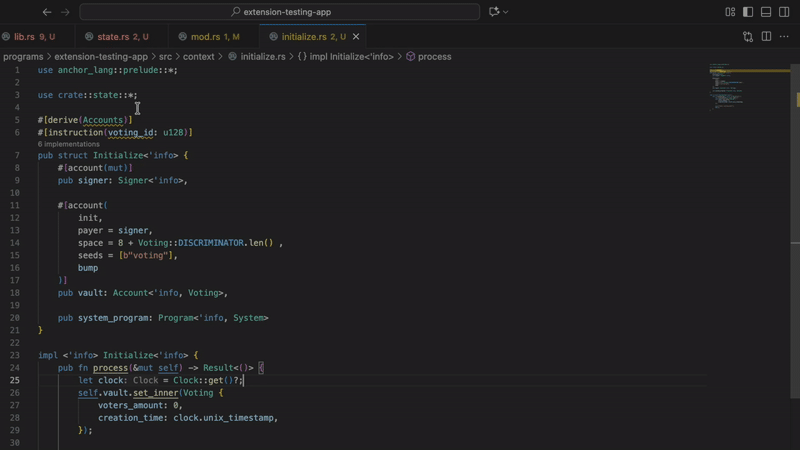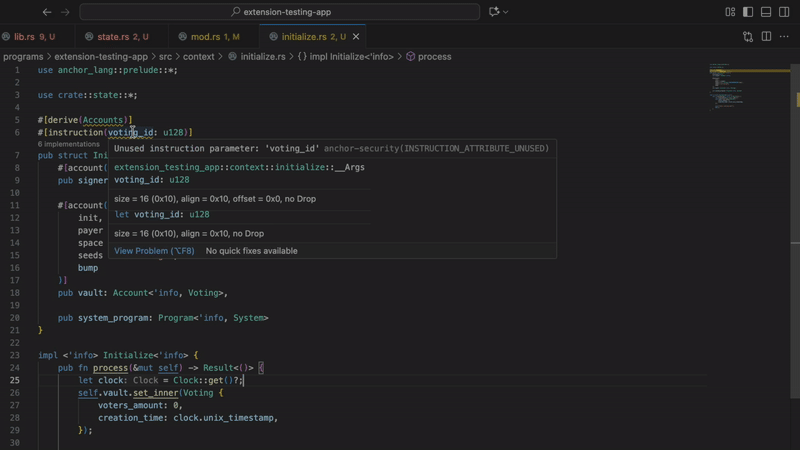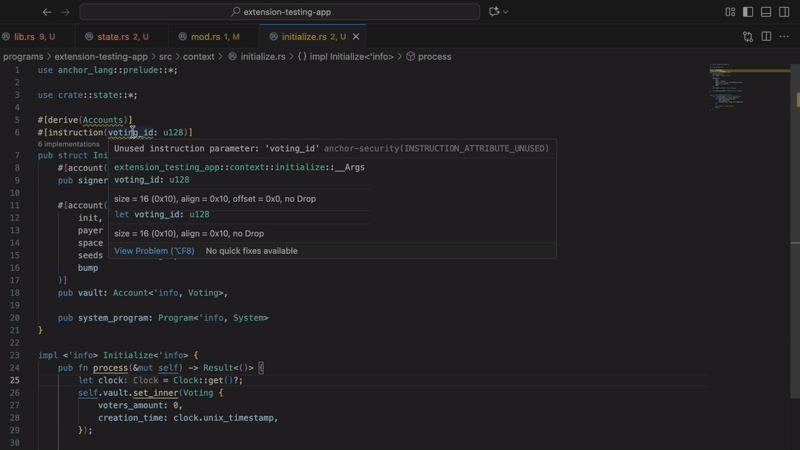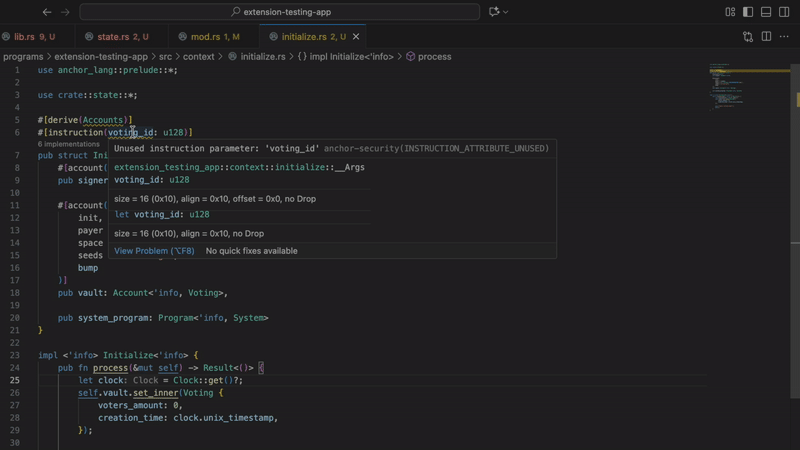
- Unused command properties
Find command properties that have been defined but have never been used. This often indicates an incomplete implementation or copy-and-paste error. Clean code means fewer bugs.
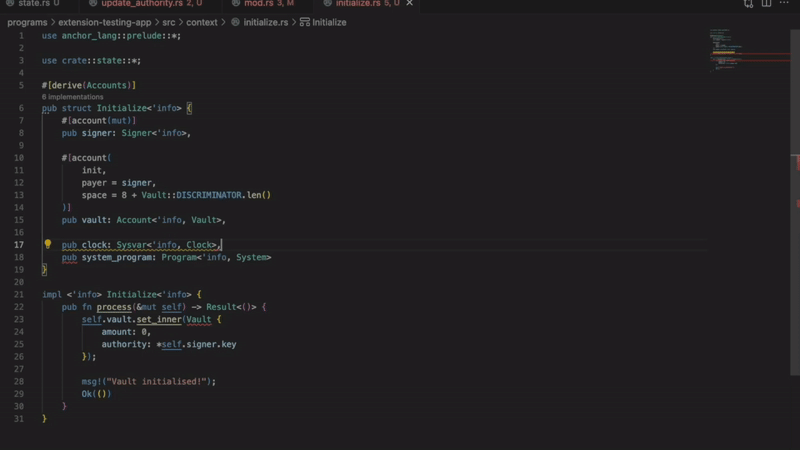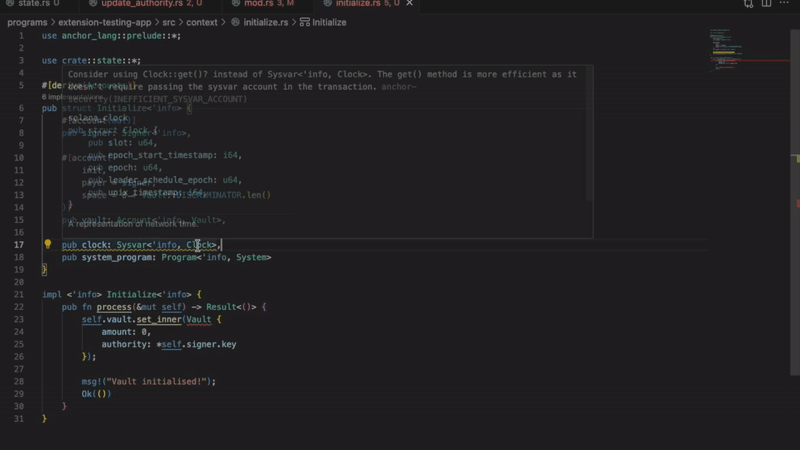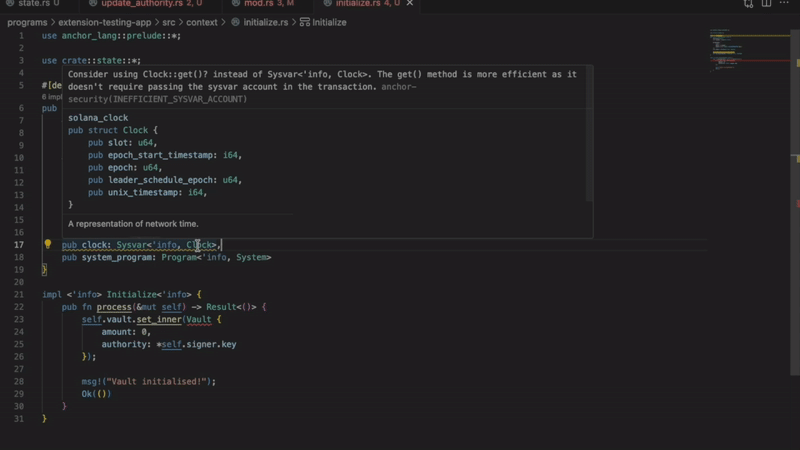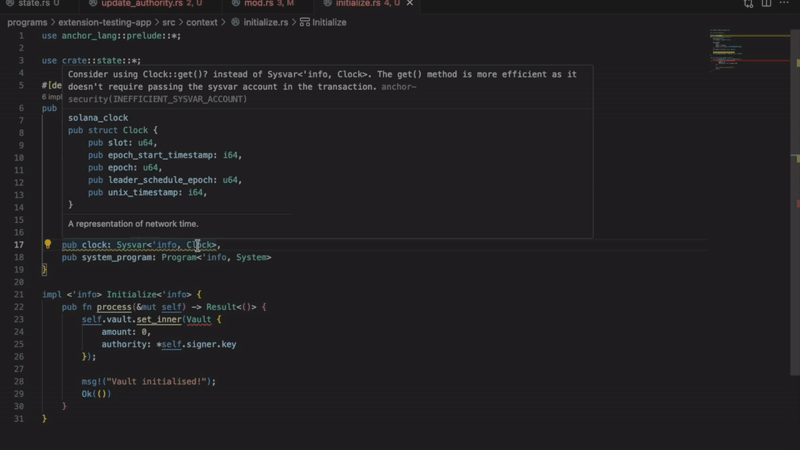
- Improper sysvar account access
Detects invalid methods of accessing the sysvar account. Using an incorrect access pattern will result in a transaction error. This extension allows you to follow Solana best practices.
- Security check comment is missing.
Flag sensitive code sections without security documentation. Important for audits and code reviews. Document why security-sensitive operations are safe.
How it works
The extension runs a Rust-based language server that parses Solana programs and applies nine detectors. Analysis occurs each time a key is pressed.
If the detector detects a problem, you will see the following:
- Red wavy line below problematic code
- Diagnostic message describing the problem
- Quick access via keyboard shortcuts (Ctrl+Alt+S / Cmd+Alt+S)
All detectors are enabled by default. No setup required.
Fuzzy range visualization
Unit tests check for specific scenarios. Fuzz testing generates thousands of random inputs to find edge cases. But without visibility, you don’t know what the fuzzer is actually testing.
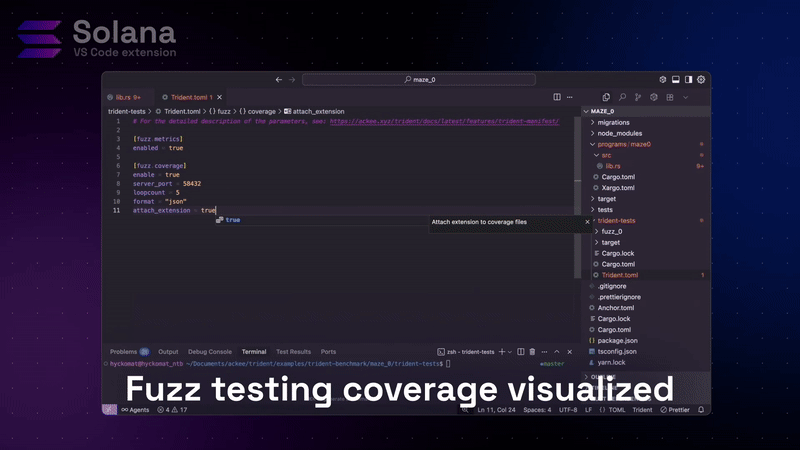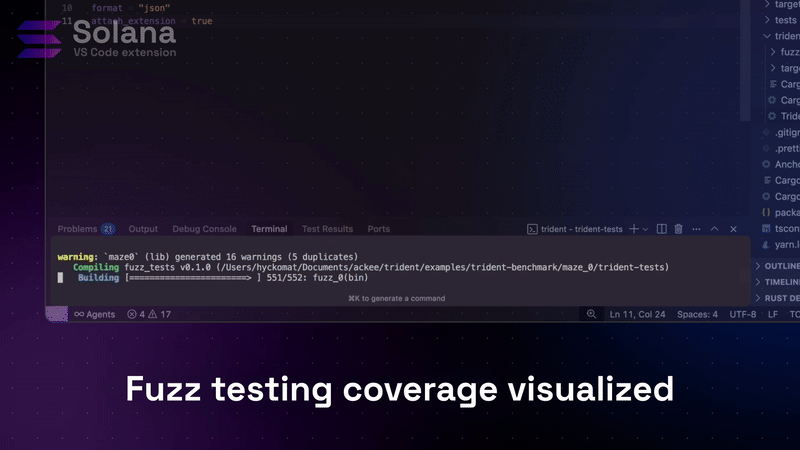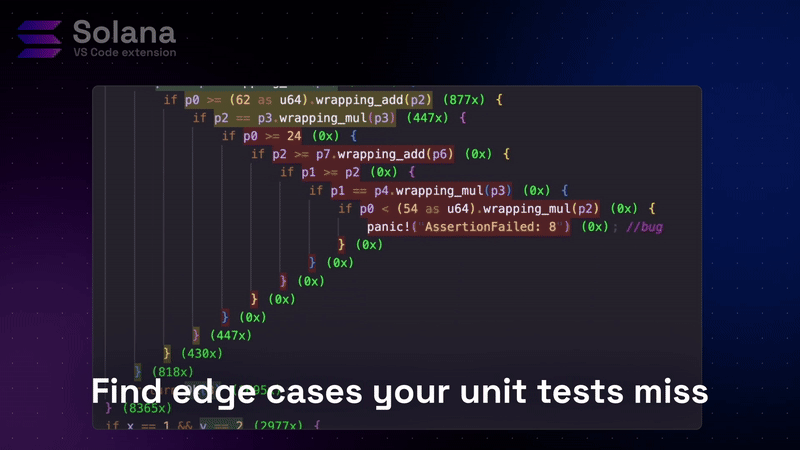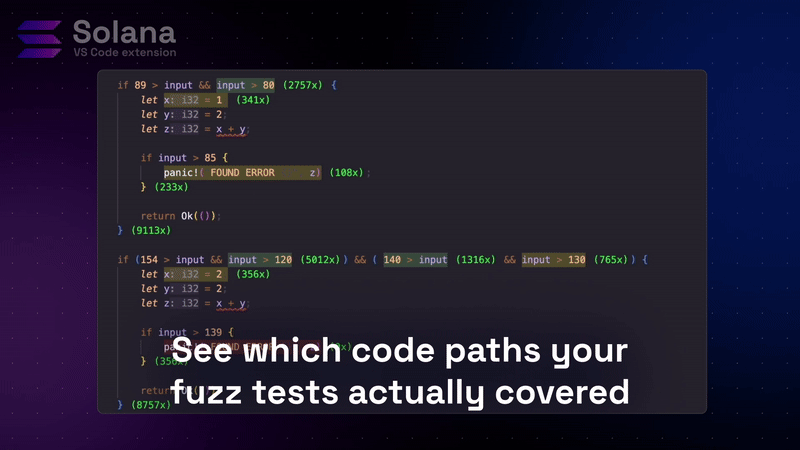
The Solana extension integrates with Trident to show you exactly which code paths are subject to fuzz testing.
Editor’s visual scope
After running a Trident test with coverage enabled, open the Coverage view in VS Code. Program code is displayed with color-coded highlights.
- green line: Included in Trident testing
- red line: untested code path
- number of executions: Number of times each line was executed
This will immediately reveal a gap. The error handling branch shows coverage as 0. Complex liquidation sequences remain untested. The overflow prevention feature is not working properly.
real case
Consider a lending protocol with deposit, withdrawal, and liquidation capabilities.
Initial coverage was green for all deposit and withdrawal operations. The team felt confident. Core features have been thoroughly tested. However, complex liquidation sequences appeared in red. Fuzzer did not run the edge case where liquidation interacts with pending withdrawals.
They added a targeted Trident flow for that scenario. We ran the coverage again. The road turned green. Then the fuzzer discovered: critical accounting bug In the clearing logic that allows double payment Under certain timing conditions.
Without coverage visualization, the bug would have been propagated to mainnet.
How to use
- Writing a Trident fuzz test
- Running tests with coverage collection enabled
- Open coverage in VS Code using the command palette
- Identify red (untested) paths
- Add a flow targeting that route
- Rerun and see improved coverage
- Repeat until the critical path is included.
As you modify your tests, the visualization updates in real time. No extra tools or context switching required.
Why we need this
Solana development progresses at the intersection of fast pace and high stakes. Even experienced developers miss things. Something is missing from the code review. Unit tests are missing edge cases.
This extension does not replace audits or comprehensive testing. We add two more security checks before production.
Static analysis catches common bugs at input. Get instant feedback in your editor instead of waiting for your CI/CD pipeline or discovering issues during a costly audit.
Coverage visualization shows gaps in fuzz testing. Understand what your tests actually do, identify what you’re missing, and test with intent rather than hope.
Think of it as defense in depth.
- Layer 1: Anchor Framework Constraints
- Layer 2: Static Analysis (this extension)
- Layer 3: Fuzzy Range Visualization (this extension)
- Tier 4: Integration testing
- Layer 5: Security Audit
This extension adds layers 2 and 3. All layers work together. A single layer is not enough.
Built by the auditor
The nine detectors come from actual results from a Solana production audit. They catch problems that cost the protocol millions of dollars. Coverage visualization is integrated with Trident, a fuzzing framework built and used for security testing in Solana programs.
We created these tools because we needed them. This feature is now available to all Solana developers.
Installation method
The extension is currently available in the VS Code Marketplace.
Option 1: VS Code Marketplace
- Open VS Code
- Go to extension (Ctrl+Shift+X / Cmd+Shift+X)
- Search for “Solana”
- Open first result (Developed by Ackee Blockchain Security)
- Click Install
Option 2: Command line
password –Installation extension ackee.solana
Requirements:
- Visual Studio Code 1.96.0 or later
- Rust and Cargo for security scanning (latest stable version)
- Perform Trident testing on your workspace for coverage capabilities.
Quick Start Command
After installation, access the feature via the Command Palette (Ctrl+Shift+P / Cmd+Shift+P).
- solana: Search for security issues in your workspace (Ctrl+Alt+S / Cmd+Alt+S)
- solana: reload security detector (Ctrl+Alt+R / Cmd+Alt+R)
- solan: Show code coverage
- solana: Close code coverage
- solana: display security scan output
A security check runs automatically as you type. Coverage requires first running the Trident test.
roadmap
(Coming Soon: We are actively developing additional features based on community feedback and audit experience. @AckeeBlockchain Check for updates on new detectors, improved coverage features, and integration improvements.)
conclusion
Solana developers no longer have to choose between speed and security.
The Solana VS Code extension adds real-time security analysis and fuzzy coverage visualization directly to your workflow. Look for vulnerabilities while coding. Check for gaps in test coverage. Deliver with confidence.
It’s free and open source. Works with all Solana projects. Integrates with existing workflows.
Created by the School of Solana and Trident teams. Professional security tools provided by auditors that protect production protocols.
Install now from the VS Code Marketplace and find vulnerabilities before they reach production.

