Main takeout
- Lazarus Group used malware to establish a fake US company for developers in encryption industry.
- This operation represents the evolution of North Korea’s efforts to be encrypted for financing.
Share this article
According to Reuters’ new reports, North Korea’s Lazarus group campaigns and steals fake US registered companies to Fish encryption developers through the sub unit.
The company, Blocknovas LLC and SoftGLIDE LLC, have been registered in New Mexico and New York using fake Persona. Another group, Angeloper Agency, is connected to this operation but not registered in the United States.
plan
The tactics included creating a fake company, setting up a convincing online existence, and posting a list of tasks for developers.
The hacker used false identity, configuration address, and real platforms such as LinkedIn and Upwork, and attracted developers. If the applicant chose, I instructed you to take a test task or software through a fake interview.
This file contains a running malware that allows the attacker to access the victim’s system so that they can extract password, password wallet key and other sensitive data.
Russian groups used almost the same tactics in the initial campaign.
In February, BleepingComputer reported that Crazy Evil, a cybercrime group that uses Russian, has already deployed similar tactics for the goal for Crypto and Web3 job seekers.
The lower group of Crazy Evil created a fake company called Chainseeeker.io and posted a list of frauds on a platform like LinkedIn. Applicants have been instructed to download GrassCall, a malicious app designed to steal credentials, encryption wallets and sensitive files.
The adjustment is well adjusted by distributing malware using replicated websites, fake profiles and telegrams.
The FBI checks the North Korean link
KASEY BEST, director of Silent Push’s threat intelligence, said that this is one of the first known cases of establishing a legally registered company in the United States and gaining reliability.
Silent Push tracked hackers as screws and identified several victims of the campaign and identified them as the most active of the three full -scale companies that found block Nova.
The FBI seized block Novas’ domain as part of the execution of North Korean cyber actors who distributed malware using fake job posts.
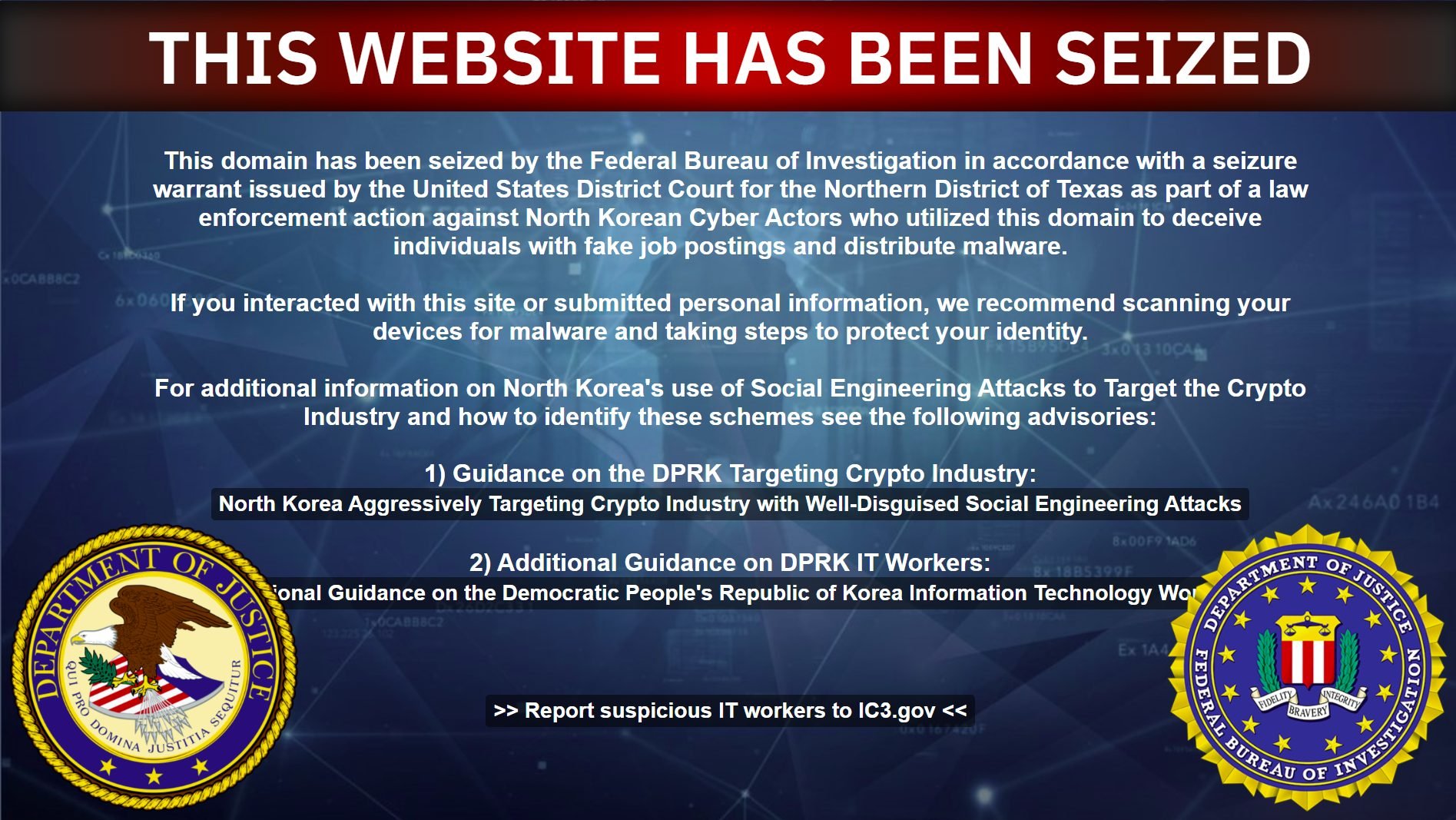

An official of the FBI said, “Everyone who promotes the ability to carry out this plan as well as DPRK actor themselves continues to focus on imposing dangers and results.
According to the FBI official, North Korea’s cyber operation is one of the most sophisticated threats in the United States.
North Korea expands the attack using the Russian infrastructure.
According to the in -depth analysis of Trend Micro, North Korea’s hacking group is to overcome limited domestic Internet access, especially Khasan and Khasan and Khasan, which are directly related to international infrastructure, especially North Korea. (Khasan) uses the Russian IP range hosted by.
Using VPN, RDP sessions, and proxy services such as Astrill VPN and CCPROXY, Lazarus Operatives can manage attacks, communicate via GitHub and Slack, and use access platforms such as Upwork and Telegram.
Researchers at Silent Push confirmed seven educational videos recorded as an account connected to the block Nova as part of the operation. This video describes how to set up commands and control servers, steal a password from the browser, upload the stolen data to Dropbox, and use tools such as Hashtopolis to crack the Crypto wallet.
From theft to spies sponsored by the state
Hundreds of developers have aimed at their sensitive credentials. Some violations appear to have expanded beyond theft, and it suggests that screws can go over other state teams for espionage purposes.
The US, South Korea, and UN officials confirmed that North Korean hackers have deployed thousands of IT workers abroad to produce millions of funds for Pyongyang’s nuclear missile programs.
Share this article

